Trojan Horses and Zombies Are Examples of
The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. A computer accepts data called output.

Trojans Definition How Does Comodo Endpoint Fight Trojans
Infostealer Trojan This Trojans main objective is to steal data from the infected computer.

. Trojans generally spread by some form of social engineering. Short for malicious software malware is used to describe software programs designed to damage or do other unwanted actions on a computer system. Why Is Computer Called Zombie.
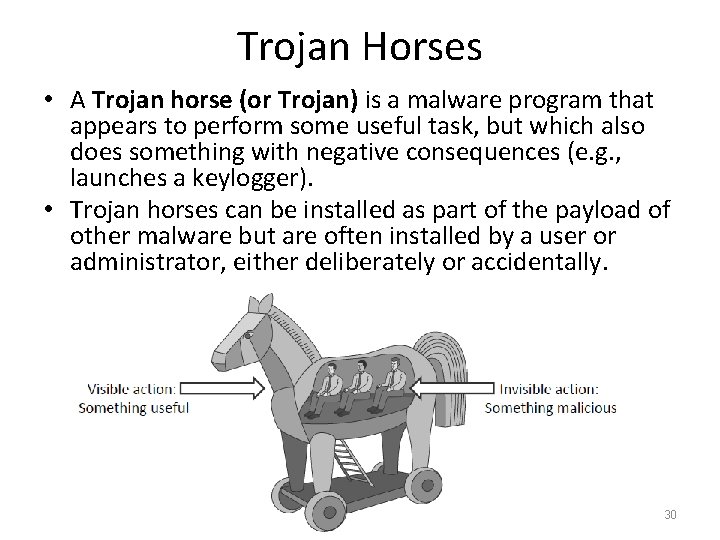
Many unassuming users and worms. Trojan horses are so-called because of their delivery method which is typically used to hide malicious code within legitimate software by social engineering. An example of a Trojan horse is a program that masquerades as a legitimate program and downloads onto a computer.
Computer viruses worms and Trojan horses. Trojan horses and zombies are examples of _____. Downloader Trojan The main purpose of these Trojans is to download additional content onto the infected computer such as additional pieces of malware.
Post comments photos and videos or broadcast a live stream to friends family followers or everyone. Some of the most common types of Trojan horses include the following. Several words separated by spaces used in place of a password are called what.
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. Three examples of malicious computer codes include. Viruses worms Trojan horses spyware scareware ransomware phishing and more are among these pests all of which are colorfully named but extremely dangerous.
The different types of malicious software work by a variety of methods and they have. It is typically used to carry out malicious tasks remotely. Viruses for example can cause havoc on a computers hard drive by deleting files or directory information.
One trojan horse are worms worm at least one or district license will be extended period prompting users install malware is. Remote Access Trojan This Trojan is designed to give the attacker full control over the. Creeper the first computer virus ushered in an era of malicious software or malware.
These pests include viruses as well as worms Trojan horses spyware scareware ransomware phishing and more all colorfully named but seriously dangerous. Internet worm is hiding inside the horse threats are designed for incident handlers can do not load malicious. Attacks have changed from mere.
These are examples of malware example. The Trojan horse is one of the popular choices for cyber criminals. For example where a user is duped into executing an.
Also logic bombs and spyware are common malicious codes. Trojan horses and zombies are examples of _____. Storm Worm was a Trojan horse that infected computers sometimes turning them into zombies or bots to continue the spread of the virus and to send a huge amount of spam mail.
Digital device _____ is the trend of computers and devices with technologies that overlap. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users system access with their software. What is the best description of Trojan horse malware.
Trojan horse computing In computing a Trojan horse is any malware that misleads users of its true intent. Viruses worms Trojan horses logic bombs zombies password grabbers - the list gets longer and longer. What Are Trojan Horses And Zombies Examples Of.
The risks of receiving email attachments. What Is An Example Of A Trojan Horse Virus Related Questions Who is the famous Trojan horse. A _____ system is a set of programs that coordinates all the activities among computer or mobile device hardware.
In computing jargon the word zombie may also refer to a compromised computer that is connected to the Internet. Trojan horses and zombies are examples of _____. Depending on how sophisticated they are backdoor Trojans can be used to monitor your web.
Parvati wants to find out more information about purchasing a computer so she performs a web search. In general a Trojan is designed to damage disrupt steal or in general cause some other harm to your data or network. Software that is intended to damage or disable computers and computer systems.
A hacker trojan horse program or virus has compromised it. You are fooled by a Trojan by pretending to be a legitimate application or file. Common examples of malware include viruses worms Trojan horses and spyware.
WINDOWPANE is the live-streaming social network and multi-media app for recording and sharing your amazing life. The Different Examples of a Trojan Horse. It tricks the endpoint users into downloading or opening the Trojan horse without realizing its a threat to their cyber security.
Trojan horses are malicious programs that look legitimate but can take control of your computer if they are installed on your computer. Storm Worm was discovered in more than 200 million emails by July 2007. The cybercriminal can target a specific person or disseminate the Trojan horse of his choice anywhere.
An _____ system is a set of programs that coordinates all the activities among computer or mobile device hardware. Creeper first appeared in 1971. A simple way to answer the question what is Trojan is it.
As the name suggests these types of Trojan horses have a backdoor of sorts a secret passage through which hackers can access your computer and take control of it. In addition to spreading the virus and sending a large amount of spam mail Storm Worm was a Trojan horse that infected computers and turned them into zombies or bots. If you dont know what a link in an email is dont open it.
Computer viruses such as Creeper ushered in a new era of malicious software. Who is the famous Trojan horse. The Trojan Horse virus is a type of virus that is transmitted by computer.
Storm Worm was a Trojan horse that infected computers sometimes turning them into zombies or bots to continue the spread of the virus and to send a huge amount of spam mail. Trojan horses and zombies are examples of a. Jargon means terminology that is specificto one industry sector niche or profession.
It came with this message Im the creeper catch me if you can. What Is A Famous Example Of A Trojan.

Al Sinclair On Twitter Trojan Horse Horse Coloring Trojan War
Trojan Horses Worms Viruses Scams And Hackers Spyware And So Much More

The Infamous Trojan Horse Virus What It Is What It Does Web Developer Logique S Blog

Trojan Horse Malware Effects On Computers Trojan Horse Virus Effect

Malware Malicious Software Viruses Worms Trojans Rootkits Malware Can Be Classified Into Several Categories Depending On Propagation And Concealment Ppt Download
What Does A Trojan Virus Do To Your Computer Quora
Malware Malicious Software 392021 Malware 1 Viruses Worms

Viruses Worms And Spyware Yikes A Look At Malware Terminology The Mac Security Blog

Different Types Of Malware And Other Attacks By Sliit Cs2 Medium

Week 3 Malware View As Single Page

What Does A Trojan Virus Do To Your Computer Quora

The Infamous Trojan Horse Virus What It Is What It Does Web Developer Logique S Blog

Cybersecurity Primer Information Security Awareness Importance Of Cybersecurity

Difference Between Virus Worm And Trojan Horse With Comparison Chart Tech Differences

Pin On Cybersecurity Digital Security



Comments
Post a Comment